Network Structure prone to frequent distruptions
Network structure prone to frequent disruptions has the following similarities.
- Difficult to know the impact area caused by incident
- Difficult to find the root cause
- Difficult to know the route for the certain traffic
- There will be huge L2 looping to cripple the entire network
Main cause of this messy structure of network is commonly from non-layered design. Layered network model is the design allocating the network components by the function such as Access layer, distribution later and core layer.
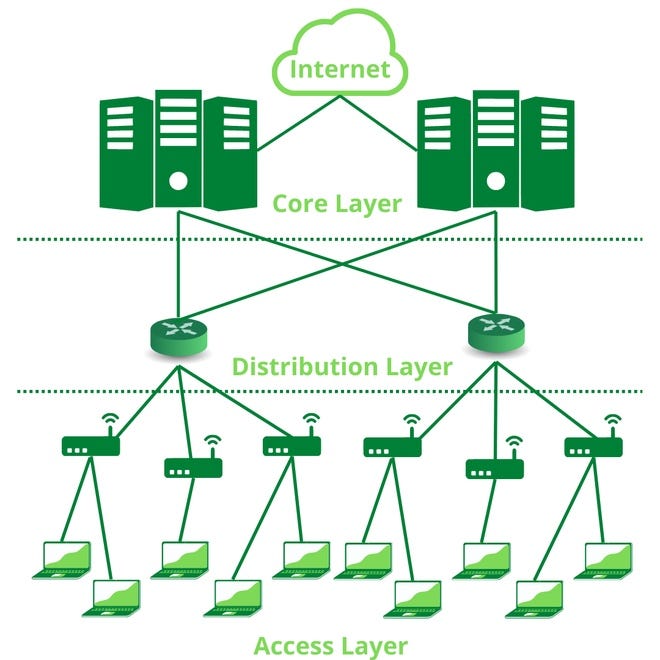
(Ref: https://www.geeksforgeeks.org/three-layer-hierarchical-model-in-cisco/)
Access Layer:
The access layer is where endpoints such as PCs are directly connected. Once authentication is completed, it performs L2 switching and, in some cases, routing and security functions as well. The key technologies used in the access layer include:
1) Security (Authentication, VLAN, Filtering): These technologies ensure secure access to the network. Authentication verifies the identity of users or devices before granting access. VLANs (Virtual Local Area Networks) are used to segment the network and isolate traffic. Filtering controls the flow of data by allowing or blocking specific types of traffic.
2) Loop Control: Loop control mechanisms prevent loops in the network, which can cause broadcast storms and degrade network performance. Spanning Tree Protocol (STP) is commonly used to manage loop prevention and provide redundant path selection.
3) Power over Ethernet (PoE): PoE allows network devices, such as IP phones, wireless access points, and security cameras, to receive power and data over the same Ethernet cable. This eliminates the need for separate power sources and simplifies installation.
Distribution Layer:
The distribution layer aggregates devices in the access layer and acts as a relay for traffic to the core layer. It also plays a role in integrating various network services and can be connected to firewalls or load balancers. It serves the purpose of preventing the creation of a large L2 network spanning the core layer.
1) Load Balancing: The distribution layer helps distribute network traffic evenly across multiple devices, ensuring efficient utilization of resources and preventing bottlenecks.
2) Scalability: It provides the ability to scale the network by allowing the addition of more access layer devices without affecting the core layer. This enables easy expansion as the network grows.
3) High Availability: The distribution layer enhances network reliability and availability by providing redundant paths and alternate routes. It ensures that if one device or link fails, the network can still function by rerouting traffic through alternate paths.
4) Security: The distribution layer can be connected to security devices such as firewalls, intrusion detection systems, or virtual private networks (VPNs) to enforce security policies and protect the network from unauthorized access or malicious activities.
Core Layer:
The core layer consolidates the devices of the distribution layer and performs the role of rapidly and accurately delivering massive traffic. Depending on the network scale, the transit layer and core layer are sometimes combined to form a two-tier architecture. The key elements are as follows:
1) High-speed traffic transmission: The core layer possesses the capability to handle large volumes of traffic with high-speed transmission. In large-scale networks, where numerous users or devices engage in simultaneous communication, fast transmission speed is essential. The core layer supports efficient traffic delivery through features such as high-speed links, bandwidth management, and packet processing.
2) Scalability: The core layer needs to have a scalable structure that can accommodate the network’s scale. In large-scale networks, where the number of users and volume of traffic consistently increase, the core layer should offer flexibility for expansion by adding new devices or links.
3) High availability: As the core layer represents the critical part of the network, high availability is of utmost importance. Any failure in this layer can have a significant impact on the entire network. Thus, the core layer must ensure reliability by employing various availability and recovery techniques. These may include redundant devices, multiple path configurations, fault detection and recovery mechanisms, among others.
Depending on the network scale, it is possible to combine the transit layer and core layer into a two-tier structure. This approach is used in smaller networks to achieve a simpler architecture and cost reduction. However, in large-scale networks, it is more common to separate the distribution layer and core layer, maintaining a hierarchical structure.
